Applications Overview
Managing Cloud Applications and Software Solutions in the Applications Module
Overview
The Applications Module allows an organization to track and manage cloud applications and software solutions that create, receive, maintain, or transmit Electronic Protected Health Information (ePHI).
Unlike device-specific inventories, this module is org-wide and focuses on primary software solutions rather than individual programs installed on each device. Examples include:
-
Email Providers: Microsoft 365, Google Workspace
-
Cloud Storage Solutions: OneDrive, Google Drive, Dropbox
-
Practice Management Software, EHR Systems, Communication Platforms
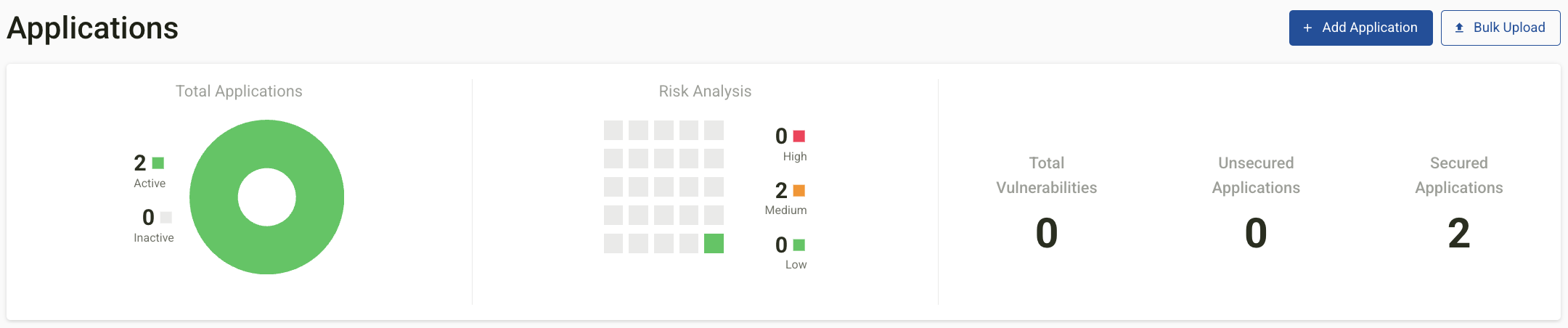
TABLE OF CONTENTS
- Overview
- Adding a New Application
- Viewing and Managing Applications
- Filtering Applications
- Managing Application Status
- Adding Evidence to Applications
- Ongoing Application Management
Adding a New Application
To add a new application:
-
Navigate to the Applications Module.
-
Click + Add Application.
-
Enter the application details in the form fields provided.
Application Information Fields
| Field Name | Description |
|
Application Name (Required) |
The name of the software or solution (e.g., Microsoft 365, Google Drive). |
|
Application Type |
Select the type: Cloud Application, On-Premise Application, or Desktop Application. |
|
Location |
Specify where the application is used (Org-wide or specific sites). |
|
License Type |
If applicable, enter details about the license or versioning. |
|
License Number |
Accompanies the License Type field, if applicable. |
|
BAA with Vendor |
Indicate whether a Business Associate Agreement (BAA) exists with the vendor. |
|
Administrator |
Select the primary administrator responsible for managing the application. |
|
Employee Access |
Define who has access: Everyone, Departmental, Management, or Some Employees. |
|
Security Controls (Required) |
Identify security measures in place for the application. |
|
Risk Rating |
Assess the likelihood and impact of a security risk related to the application. |
|
Status |
Indicate whether the application is Active or Inactive. |
|
Notes |
Add additional details or security-related considerations. |
Security Controls Fields
| Control | Description |
|
Encryption |
Does the platform encrypt data at rest/in transit? |
|
Antivirus/Malware Protection |
Is the application protected against malicious threats? |
|
Strong Password Requirement |
Does the application require strong passwords? |
|
Multi-Factor Authentication (MFA) |
Is MFA/2FA enabled for access? |
|
Backups |
Does the organization back up data stored in this platform? |
* Important: Security controls may vary depending on the vendor. Organizations should confirm directly with the vendor to ensure proper security measures are in place.
Bulk Upload Option
To add multiple applications at once:
-
Download the Bulk Upload Template.
-
Fill in all required fields.
-
Upload the completed spreadsheet into The Guard.
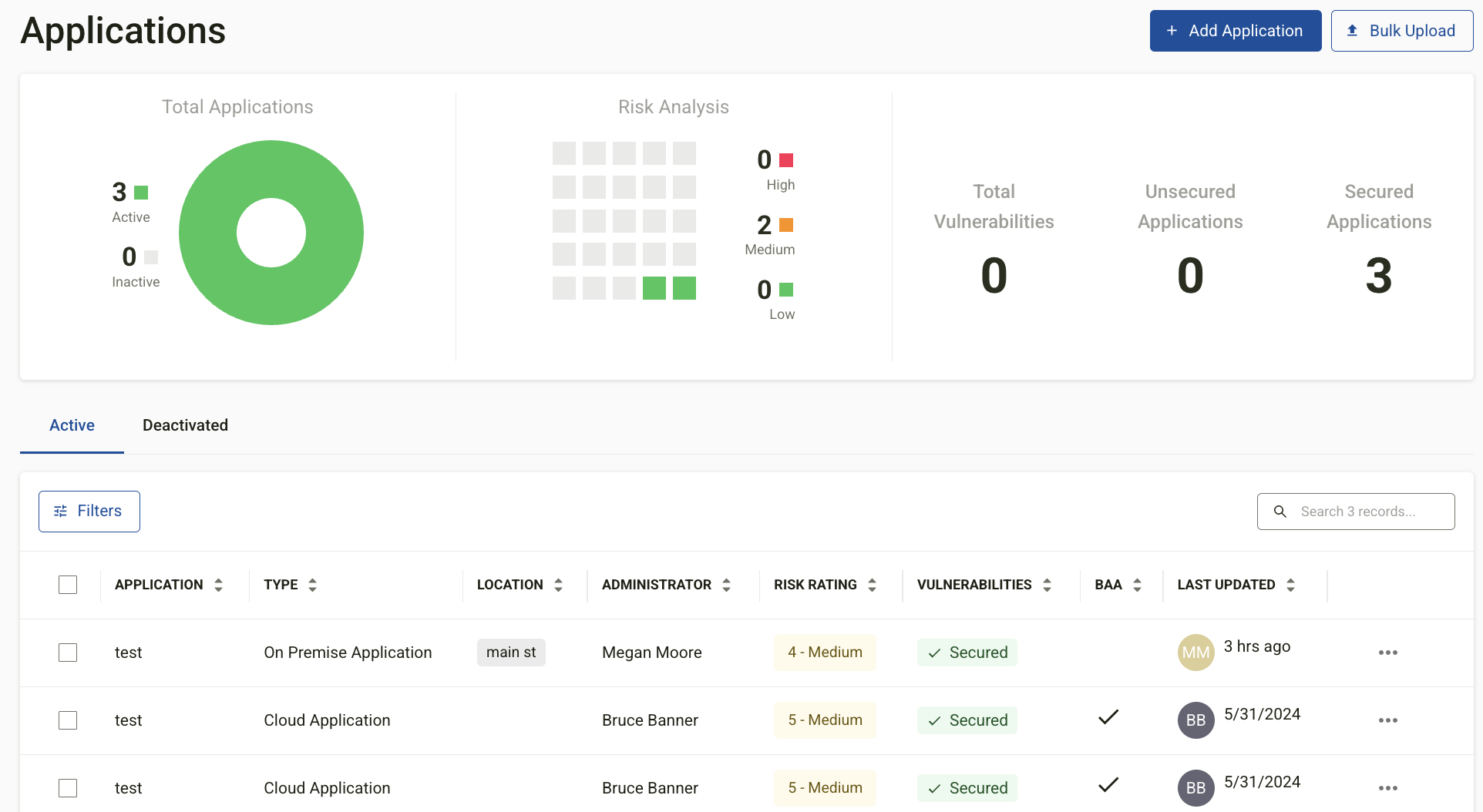
Viewing and Managing Applications
Once applications are added, they appear in the application inventory list within the Application Module.
Application Inventory List Display
The list displays:
-
Application Name
-
Type
-
Location
-
Administrator
-
Risk Rating
-
Vulnerabilities
A graph at the top of the page provides a summary of:
-
Total Applications (Active, Inactive)
-
Risk Analysis
-
Total Vulnerabilities
-
Secured vs. Unsecured Applications
Filtering Applications
Filters can be applied to refine the list by:
-
Active/Inactive Status
-
MFA
-
BAA with Vendor
-
Encryption
-
Endpoint Protection
-
Risk Rating
-
Strong Password Requirement
-
Backups
-
Location
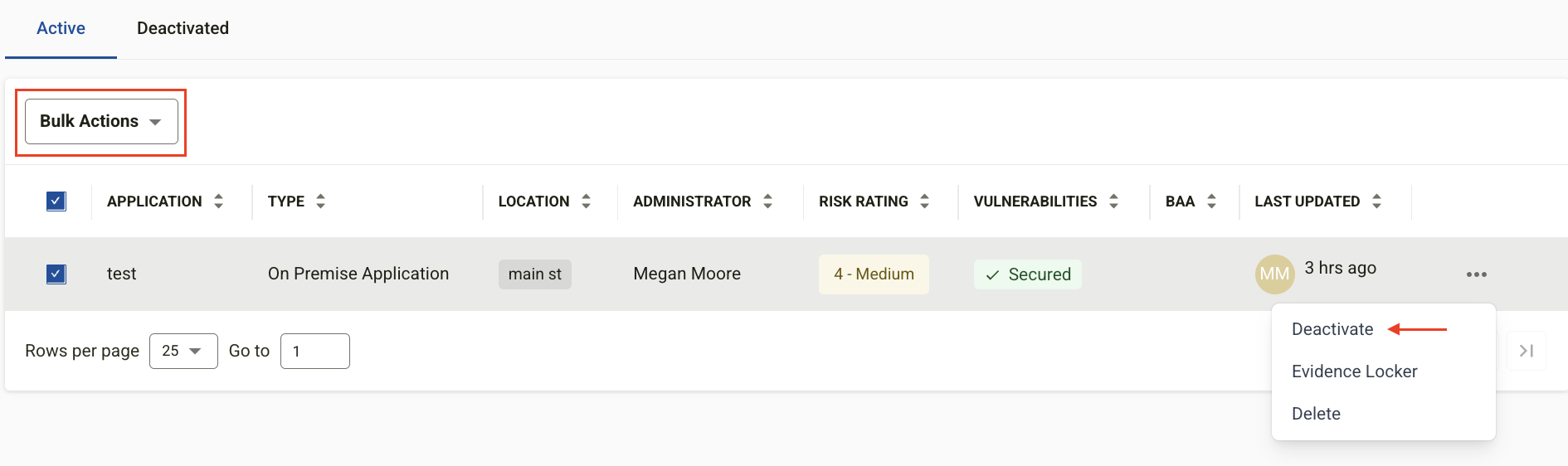
Managing Application Status
Applications can be set to Inactive when no longer in use.
Bulk Status Updates
-
Select the checkboxes of applications to update.
-
Click Bulk Actions and choose Deactivate.
Individual Status Updates
-
Click the ellipsis button next to an application.
-
Select Deactivate from the options.
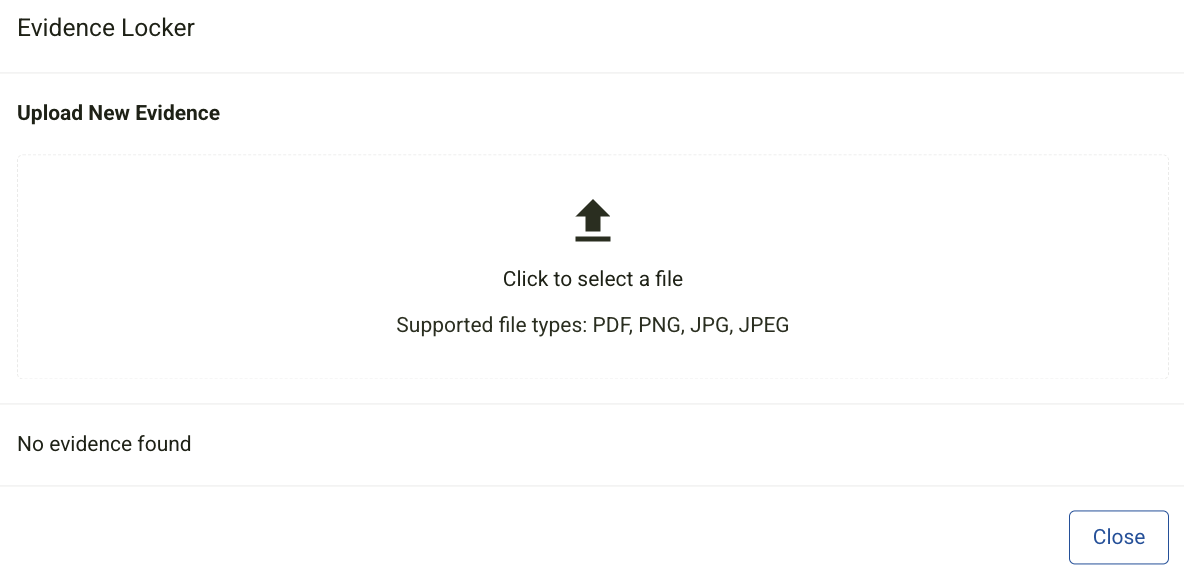
Adding Evidence to Applications
To attach supporting evidence:
-
Click the ellipsis button next to an application.
-
Select Evidence Locker to upload relevant files.
Ongoing Application Management
Application inventories should be regularly updated to ensure compliance, security, and risk assessment remain accurate.
Modified on Mon, 28 Jul at 11:57 AM
.png?width=2000&height=500&name=Compliancy%20Group%20logo%20(3).png)